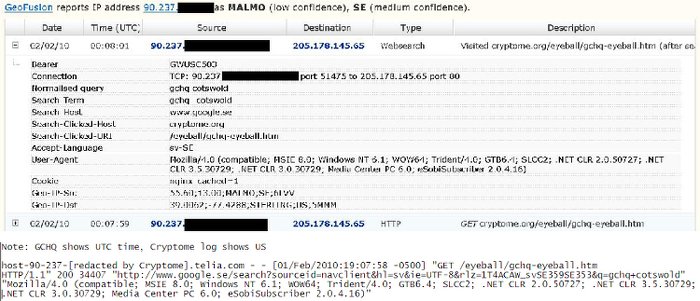
October 2, 2015 - A few days ago, a new Snowden slide was released that appeared to show that the GCHQ was monitoring Cryptome in near-real-time by examining the browsing data of one of the websites' visitors. John and Deborah of Cryptome later verified that the information in the slide matched their logs, which seemingly verified the legitimacy of the slide and the information presented about KARMA POLICE.


However, after examining the slide and all the information available, I realized that it was possible to create the slide (or one like it) with accurate data without any of the sources cited/assumed/alleged. To demonstrate this, I put together some comparable information. To respect the privacy of visitors to Cryptome, the end of each IP address is redacted and I've provided only a little information about several users instead of focusing on one user to provide detailed information about.
A few notes before getting into the data:
IP: 212.48.158.*
Date: 2010-02-10
Time: 23:06:15
URL: http://cryptome.org/cartome/foucault.htm
Note that I manually translated the time and date from a time code, so it may be slightly incorrect. The original timestamp was 20100210230615.
In case I mistranslated the timestamp or anyone thinks that it was a fluke, here are twelve time and dates along with the redacted IP address that visited Cryptome at that time. These time and dates were originally rendered in a human readable format, so there is no danger that I mistranslated them.
Finally, a semi-obscure phrase from the that was put into a search engine - complete with the original typo.
"architectural engineering in miidle east" - it may appear in the logs as "architectural+engineering+in+miidle+east"
All of this information should be readily verifiable by John and Deborah at Cryptome, demonstrating that each of the pieces of the slide could have been created without the benefit of a surveillance program or large budget. In other words, the guilty knowledge implied by the accuracy of the slide can imply things other than being guilt of surveillance.
Update October 6, 2015 15:51 Eastern: Cryptome replied by email, saying "You're doing well on this on your own. Keep at it."
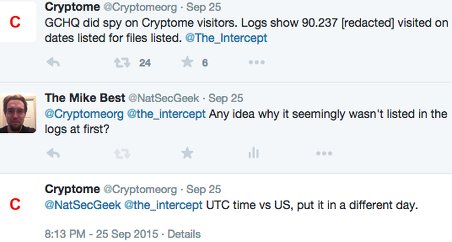
21:12 Eastern: Cryptome has not contradicted the accuracy of my findings or denied the presence of the IP addresses listed in their logs at the specified times. Cryptome quickly denied the presence of the IP address listed in the slide released by The Intercept in their logs, then confirmed it after accounting for the time zone.
Update October 7, 2015 09:29 Eastern: Cryptome has indirectly confirmed my findings, saying "You are attacking like the spies, sanctimonious, invading users, stealing data."
@NatSecGeek You are attacking like the spies, sanctimonious, invading users, stealing data.
— Cryptome (@Cryptomeorg) October 7, 2015Of course, no data was stolen - it was quite legitimately found. Cryptome then blocked my account on twitter.
Cryptome uses several infosec systems, PK just one. Open to more. Compromise should be publicized but seldom is: hide, deny, ignore, delude.
— Cryptome (@Cryptomeorg) September 16, 2015More importantly, if they won't directly confirm the validity of the data, is there any other way to validate it than to release the unredacted data and the method to the public? Alternative suggestions are most welcomed.
Update: Cryptome has denied that saying the data is stolen implies that it is accurate. See here for my response along with the data.
Update: Cryptome has finally confirmed the information is accurate.